Hi, am using docker and the Sierra Leon test database version 2.40.4.1 and postgis 13.
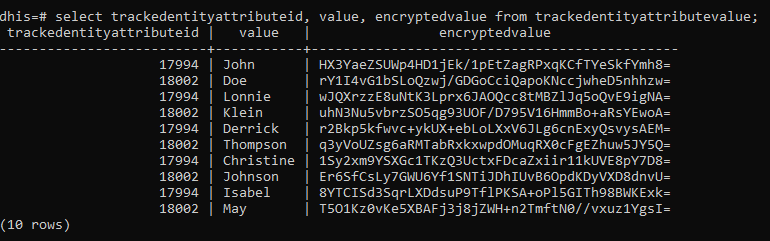
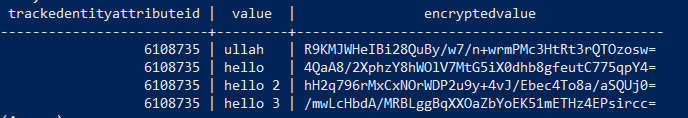
After trying to set an existing attribute as confidential and getting this error:
“Confidentiality option not available since encryption is not configured”
TEST 1:
I went into dhis.conf I added the following lines:
encryption.password = mylongencryptionpassword123
After restating, I get the same error. Dhis.log, has nothing.
TEST 2:
I went into dhis.conf I added the following lines:
encryption.password = myshortpassword
After restating, I get the same error. I get a Warning on dhis.log, that says that my encryption password is too short - which is expected as per the docs. This indicates that the variable is indeed being read.
TEST 3:
I went into dhis.conf I added the following lines -including a password that is over 24 chars long:
encryption.password = mylongencryptionpassword123
logging.level.org.hisp.dhis = DEBUG
logging.level.org.jasypt.encryption = DEBUG
After restarting, clearing cache, I went back to confidentially option and still got the same error message saying that is not configured. The same error is also displayed when trying to add a new TEA.
dhis.log only shows the lines below, no mention of encryption, and no errors are logged.
- INFO 2024-07-19T17:31:10,675 Added logger: org.jasypt.encryption using level: DEBUG (Log4JLogConfigInitializer.java [main])
- INFO 2024-07-19T17:31:10,675 Added logger: org.hisp.dhis using level: DEBUG (Log4JLogConfigInitializer.java [main])
Any ideas of what am missing or how else to debug this error?
thank you!