By @ibrahimwickama , @vincentminde , Fidelis Ronjino and et al.
Greetings! My name is Ibrahim Wickama from Tanzania, I am a Senior System Developer at the University of Dar es Salam (UDSM). Through the UDSM DHIS2 Lab, I have consulted widely in the area of Information Systems, including implementation of government systems in the Health, Social Welfare and Agricultural Sector, using the DHIS2.
I would like to invite you to my presentation during the Annual Conference session named DHIS2 Security and Policy planned on Tuesday 13 June, 15:30-17:00 Oslo time zone . You can go through overview of my presentation below.
Overview
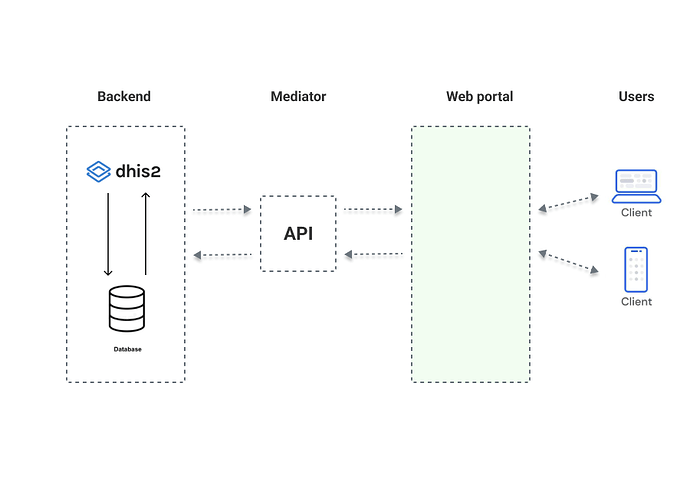
It is crucial undertaking in ensuring the integrity and confidentiality of sensitive data within the DHIS2 system. DHIS2 serves as a data collection, management, and analyze data. While the system offers powerful capabilities, its APIs can present security challenges when accessed directly by web portals due to potential vulnerabilities and risks associated with direct exposure.
To mitigate these security challenges, the use of mediators becomes essential. Mediators act as intermediaries between the web portals and the DHIS2 APIs, providing an additional layer of security and control over data flow. They act as gatekeepers, ensuring that only authorized and validated requests are passed through to the DHIS2 APIs. By implementing mediators, organizations can enforce strict authentication and authorization protocols, validate incoming requests, and apply necessary data transformation and encryption techniques to secure the communication channel.
With security policy measures in mind to secure the whole architecture and communications, considering key aspects like:
- Authentication and Authorization in mediator and DHIS2 backend.
- Secure Communication and hidden sensitive data.
Security reinforcements
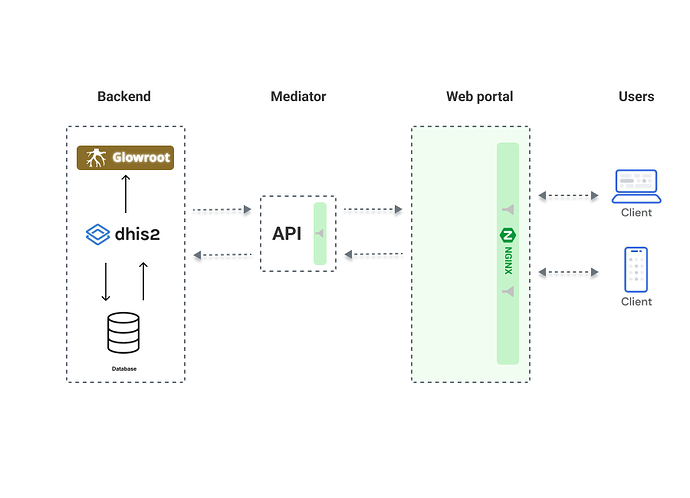
To further reinforce the security measures mentioned in the previous paragraph, additional safeguards such as Nginx URL filtering, mediator API payload inspections, and DHIS2 monitoring using tools like Glowroot can be implemented.
-
Nginx URL filtering: Provides an additional layer of protection by allowing organizations to define strict rules for filtering and blocking certain types of requests or URLs. By configuring Nginx to filter incoming requests based on predefined patterns or rules, organizations can mitigate common security threats such as SQL injection, cross-site scripting (XSS), and directory traversal attacks. This helps to prevent malicious actors from exploiting vulnerabilities in the web portal or DHIS2 APIs.
-
Mediator API payload inspections: Involve thorough examination and validation of the incoming API requests and their payloads. By implementing payload inspections within the mediator, organizations can analyze the data being sent to the DHIS2 APIs, ensuring it adheres to predefined standards and is free from malicious content or potential security risks. This inspection process can include checks for data consistency, format validation, and the identification of any suspicious or unauthorized content within the payloads.
-
Serious DHIS2 monitoring: Tools like Glowroot. Glowroot is a lightweight performance monitoring and profiling tool specifically designed for Java applications. By integrating Glowroot with DHIS2, organizations can gain real-time visibility into the system’s performance and identify any potential security vulnerabilities or anomalies. This includes monitoring key metrics such as response times, database queries, and memory usage, which can help detect and mitigate potential security incidents in a timely manner.
Conclusion
In summary, addressing the security challenges of DHIS2 APIs through mediators to web portals is essential for safeguarding the integrity and confidentiality of sensitive health data. Security is a race against time, vulnerabilities may exist long before you discover them. Act with urgency to identify and patch vulnerabilities before they are exploited.